Trendaavat aiheet
#
Bonk Eco continues to show strength amid $USELESS rally
#
Pump.fun to raise $1B token sale, traders speculating on airdrop
#
Boop.Fun leading the way with a new launchpad on Solana.
40-year retrospective on elliptic-curve cryptography happening now: 🤓
Hehehe, Neal Koblitz talking about how "the appearance of a proof impresses people" and how "people's approach to mathematics is too superficial"🤘
Neal highlighting the increase of anti-intellectualism in the US.
Steven Galbraith: "Basically ECC has held up as much as we could've hoped for in 40 years of cryptanalysis."
Victor Miller: "I'm gratified that [...], except for a hypothetical quantum computer, it held up."
Neal Koblitz roughly says we should be skeptical of assuming hardness of problems that have not seen practical computational attempts at breaking it.
(Earlier he pointed to LWE reductions having huge gaps.)
Victor Miller: "There aren't too many people working on cryptanalyzing isogenies"
Steven Galbraith (laughing getting up from his chair): "I am, I am!"
Galbraith: "Advice for students?"
Victor Miller: "You have to really be enthusiastic about something. So go with something that really speaks to you! [...] Even if it doesn't look like it has anything to do with anything. [...] It's gonna pay off"
Neal Koblitz: "You need some critical thinking ability in going from mathematics to cryptography. The danger is superficiality in the analysis.
The habit of doing that [critical thinking] will prevent you from making serious errors or overlooking others."
Dan Boneh recommends this "Diophantus and Diophantine Equations" book by Bashmakova 👇
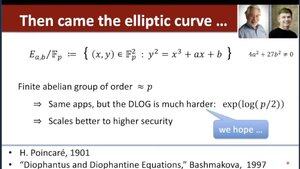
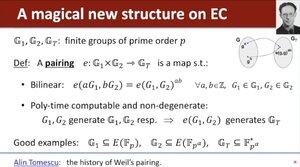
...and Dan mentions my historical summary on pairings:
🫡🥲🥹
And, naturally, the simple, beautiful and extremely-versatile BLS signature scheme 👇
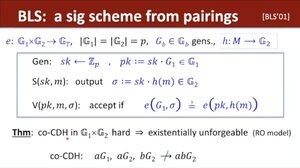
(Shameless plug: You should (almost-)always aggregate t-out-of-n BLS signatures using the faster t\log^2{t}-time algorithm: )
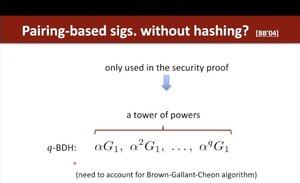
Dan mentions Boneh-Boyen signatures which do not require hashing, although they need a stronger assumption 👇

Dan remind us that powers-of-tau make it easier to compute discrete log on tau 👇
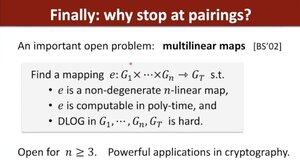
Dan asking all of us to not stop and work on multilinear maps, which are now at least 23-years old!
"I'm almost convinced someone on the planet knows the answer, and we haven't found that person yet."
Dan: "When we talk about post-quantum, we have to separate it into _encryption_ and _everything else._"
"For encryption, because of harvest-now-and-decrypt-later attacks, it's important that we transition quickly."
"For integrity mechanisms, there's still quite a bit of time."
Dan reminds everyone of the huge honey pot available for anyone who builds a quantum computer:
Satoshi's initial (currently-unspent) Bitcoins!
"I am a very strong proponent of hybrid [post-quantum] deployments. We have actually seen a number of NIST [post-quantum] candidates even some of the finalists get broken with a **pre**-quantum attack."
Dan says "[We need to] encourage people to study the post-quantum security of the post-quantum [cryptographic] systems" and reminds us of the recent LWE scare with a potential quantum algorithm (that fortunately ended up being wrong).
Galbraith compares the 8-page CRYPTO papers from the 80s with today's 34-page CRYPTO submissions.
Dan: "Something is going to break at some point. Our community is growing. More people doing research => more papers => more pressure on committees, on paper writers, on everybody. I
would view this as a success of the community. I would celebrate that.
How to deal with this growth? Every successful field has had it and dealt with it (e.g., machine learning). Confident we will deal with it."
(Out-of-context) Dan: "Work harder."
Kristin Lauter on the history of ECC at Microsoft 👇

ECC was deployed for the first time in Windows Vista in 2005.
Oh, how great were those days of the early internet... 🥹🥹
Kristin Lauter: "BLS signatures can be used to prevent pollution attacks in CDNs like BitTorrent" 👇

Kristin Lauter on the quantum threat 👇
"With m = 256, you're looking at needing roughly 1,500 [logical, high-fidelity] qubits on a quantum computer."

Kristin Lauter on isogeny-based cryptography, introduced by Steven Galbraith in '05 👇

....aaaand that wraps the retrospective (see for the full program)!
I salute 🫡 all the brave intellects who brought us this far, and I eagerly await for those damn multilinear maps to be ready, so I can build my SMURFs 😆:
Oh, but wait, I missed Victor Miller's talk! 😭
Let me see if I can summarize some gems from there too...
Victor Miller starts with a nice quote: "Fortune favors the prepared mind!" 👌👌
My interpretation: So, read as many crypto papers and math textbook as you can?
"What was interesting is, when I got to Harvard, I, at the time was the only graduate student there [...] who really had any facility with computation."
Don't feel alone.
So many mathematicians.
I never understood the obsession with avoiding death, but if there ever was a reason... it's to not lose progress in math!
(What if there was a simpler proof of Fermat's last theorem?)

Victor mention's Coppersmith DL algorithm for GF(2^n) and how he started thinking of work-arounds...

Why we're all verifying zkSNARKs in 1 millisecond these days 👇

Apparently, in 2000, some folks thought elliptic-curve cryptography was a meme.
Encouraging for blockchains, I say!
Victor concludes that it's always good to study arcane things like elliptic curves or number theory
You never know what's gonna actually be practical or useful a decade later.

Back to Neal Koblitz's talk: he first got into cryptography in 1979 due to a teaching curiosity about RSA!
He wanted to better motivate his number theory course for his students and thought RSA was a great way to do it! 💕

Later on, Lenstra's elliptic-curve factoring algorithm that really grabbed Koblitz 👇

So, Koblitz started wondering: can I use these fancy-shmancy algebraic geometry objects to *construct* (rather than destruct) cryptography?

Koblitz recalls how doing crypto back in the day was a sort of rebellious act.
And this liveliness and free-spiritedness showed:
e.g., a "restriction" at the CRYPTO rump session meant that you could only throw *empty* beer cans at the speakers 😂😂
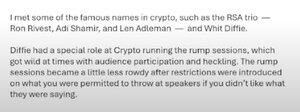
This of course, has changed.
But, as Dan Boneh put it earlier, this should be seen as a success indicating that our field has taken off!

Alright, alright, this is really the end! 🫡
See the two recordings here:
And the full program here:
1,81K
Johtavat
Rankkaus
Suosikit













