Trendaavat aiheet
#
Bonk Eco continues to show strength amid $USELESS rally
#
Pump.fun to raise $1B token sale, traders speculating on airdrop
#
Boop.Fun leading the way with a new launchpad on Solana.
Probably the best survey of quantum computing progress was updated recently, this time to account for @CraigGidney newest paper, whose concluding line in the paper reads:
"I prefer security to not be contingent on progress being slow"
Ironic that it is a controversial belief.

7.8. klo 18.20
Sam Jaques @sejaques updated his excellent quantum landscape. Now you can quickly move between years and see the progress. This really shows what a big deal @CraigGidney algorithmic improvement this year is: moving the red line goalposts much closer!
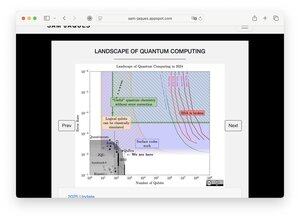
Full conclusion so I don't quote out of context:
In this paper, I reduced the expected number of qubits needed to break RSA2048 from 20 million to
1 million. I did this by combining and streamlining results from [CFS24], [Gid+25], and [GSJ24].
My hope is that this provides a sign post for the current state of the art in quantum factoring,
and informs how quickly quantum-safe cryptosystems should be deployed.
Without changing the physical assumptions made by this paper, I see no way reduce the qubit
count by another order of magnitude. I cannot plausibly claim that a 2048 bit RSA integer could
be factored with a hundred thousand noisy qubits. But there’s a saying in cryptography: “attacks
always get better” [Sch09]. Over the past decade, that has held true for quantum factoring. Looking
forward, I agree with the initial public draft of the NIST internal report on the transition to post-
quantum cryptography standards [Moo+24]: vulnerable systems should be deprecated after 2030
and disallowed after 2035. Not because I expect sufficiently large quantum computers to exist by
2030, but because I prefer security to not be contingent on progress being slow
@CraigGidney @lopp I think you expressed interest in this plot previously:


851
Johtavat
Rankkaus
Suosikit













